How to do MX, SPF, DKIM, DMARC Setup

When it comes to cold emailing, two things matter most: your email copy and your infrastructure.
While copy focuses on the offer you’re making, infrastructure is all about one factor—deliverability. This is where technical setups, like email authentication methods, play such an important role.
Whether you’re new to cold emailing or an experienced sender dealing with low inbox placement, this guide will help you master email authentication.
In this article, you’ll find everything you need to know about setting up MX, SPF, DKIM, and DMARC records, including:
- What these records are
- Why they’re important
- When to set them up
- Step-by-step instructions
Let’s dive in!
What are MX, SPF, DKIM, and DMARC records
MX, SPF, DKIM, and DMARC records are "email authentication" methods because they confirm sender identity and decide whether it comes from a reliable source or has been faked by spammers pretending to be someone else.
In simple words, these records build a trustworthy sender’s reputation. Think of it as an identity verification of your domain so that the ESPs can let your email reach the recipients' primary inbox.
MX (Mail Exchange) Records
Purpose
Directs email to your domain's mail servers.
How It Works
MX records specify which servers handle incoming emails from your domain. These records don’t directly impact outbound email authentication but ensure that your emails are routed properly to recipients.
SPF (Sender Policy Framework)
Purpose
Prevents sender address forgery.
How It Works
SPF records list all IP addresses authorized to send emails on behalf of your domain. When you send an email, the recipient’s server checks the SPF record to verify that the sending IP is legitimate.
A correct SPF setup helps keep your emails out of spam by showing you’re an authentic sender.
DKIM (DomainKeys Identified Mail)
Purpose
Confirms message authenticity and integrity.
How It Works
DKIM attaches a unique digital signature to each outgoing email, verifying the email hasn’t been altered in transit. This is done by using cryptographic keys that match the public key in your DNS with a private key on your server.
A valid DKIM signature boosts your sender's reputation and builds trust with ISPs.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Purpose
Provides visibility and control over unauthenticated emails.
How It Works
DMARC combines SPF and DKIM to specify actions if an email fails either check. With DMARC, you can choose to allow, quarantine, or reject unauthenticated emails. DMARC also provides reporting, helping you see if others are trying to spoof your domain.
When to Set Up MX, SPF, DKIM, and DMARC
Always do the email authentication process—MX, SPF, DKIM, and DMARC set up—after buying new domains and before warm-ups.
Why should Cold Email Senders do Email Authentication?
The benefits of email authentication—MX, SPF, DKIM, and DMARC records—include enhanced sender reputation, better deliverability rates, etc.
Here are the benefits in a bit more detail:
Improved Deliverability
Email providers like Gmail and Outlook use authentication to decide if an email is trustworthy. With MX, SPF, DKIM, and DMARC records in place, your sender addresses have a much better chance of reaching the inbox instead of the spam folder, which means higher open rates.
Enhanced Sender Reputation
Authentication signals to email providers that your domain is secure and verified. As email providers see this, they begin trusting your emails, making it easier for you to maintain a good sender reputation, essential for long-term cold emailing success.
Prevent Spoofing
Without authentication, spammers could forge emails to look like they’re from your domain, damaging your brand and reputation. With SPF, DKIM, and DMARC, you protect your domain from unauthorized senders, keeping your brand safe.
Increase Response Rates
When your emails are authenticated and more likely to reach the inbox, recipients are more likely to see, open, and engage with them. Better deliverability and trust lead to higher response rates, making your campaigns more successful.
Setting Up MX Records on Your Server
For specific instructions on setting up your MX Record in Google Workspace, click here and in Microsoft Office 365, click here.
For general instructions, follow this 5-step guide to set up MX records:
Access Your Domain Registrar
Log in to your domain registrar (e.g., GoDaddy, Namecheap, Cloudflare) and navigate to the DNS settings or DNS management section for your domain.
Locate the MX Records Section
In the DNS management area, find the section to add or manage MX records.
Add New MX Records
Select the option to add a new record, choose "MX" as the record type, and specify the mail server address (e.g., `mail.yourdomain.com`).
Set Priority
Assign a priority to the MX record, with lower numbers indicating higher priority. Repeat for multiple records if needed.
Save Changes
Save your new MX record settings. It may take up to 48 hours for the changes to fully propagate across the internet.
This setup should allow emails to be routed to your mail server based on the MX records you've specified.
Setting Up SPF Record on Your Server
For specific instructions on setting up your SPF Record in Google Workspace, click here and in Microsoft Office 365, click here.
For other ESPs, follow this 5-step guide to set up SPF record:
Access Your Domain’s DNS Settings
Log in to your DNS hosting provider (e.g., GoDaddy, Cloudflare, Namecheap).
Find the DNS management section where you can add or edit DNS records.
Create or Edit Your SPF Record
Look for an existing SPF record in your DNS settings. If it’s not there, you’ll need to add one.
Start the SPF record with v=spf1 to indicate the SPF version.
Add your authorized sending IPs or include other domain names authorized to send on your behalf. For example:
- ip4:192.168.0.1 if you’re specifying an IP address.
- include:sendgrid.net if you’re using a third-party service like SendGrid.
End the record with an all directive, such as -all (strict) or ~all (lenient).
Example SPF record:
makefile
Copy code
v=spf1 ip4:192.168.0.1 include:sendgrid.net ~all
Save and Apply Changes
Save the record. The new SPF record may take a few minutes to propagate, though sometimes it can take up to 48 hours.
Test Your SPF Record
Use SPF record validation tools like MxToolBox or Google’s SPF check to confirm the record is correct and is properly identifying your sending servers.
Setting Up DKIM Record on Your Server
For specific instructions on setting up your DKIM record in Google Workspace, click here and in Microsoft Office 365, click here.
For other ESPs, follow this 5-step guide to set up DKIM record:
Generate Your DKIM Key Pair
Start by generating a public-private key pair.
Many email service providers (ESPs) and platforms have built-in tools to generate DKIM keys for you. If not, you can use tools like OpenSSL to create one manually.
Access Your Domain’s DNS Settings
Log in to your DNS hosting provider (e.g., GoDaddy, Cloudflare, Namecheap). Navigate to the DNS management section where you can add or edit DNS records.
Create a New TXT Record for DKIM
Add a new TXT record.
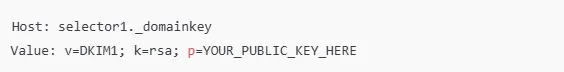
In the "Host" or "Name" field, add a prefix (often provided by your email provider) followed by `_domainkey`.
For example, `selector1._domainkey`. In the "Value" or "Text" field, paste your public key. This key should begin with `v=DKIM1; k=rsa;` followed by the actual key content.
Save and Apply Changes
Save the TXT record. DNS propagation for DKIM records can take a few minutes to a few hours.
Test Your DKIM Setup
Use testing tools like DKIMCore, Google’s Check MX tool, or MxToolbox to confirm that the DKIM record is set up correctly and active. These tools will verify that the record is properly configured and working.
Setting Up DMARC Record on Your Server
For specific instructions on setting up your DKIM record in Google Workspace, click here and in Microsoft Office 365, click here.
For other ESPs, follow this 5-step guide to set up DKIM record:
Here’s a step-by-step guide for setting up a DMARC (Domain-based Message Authentication, Reporting, and Conformance) record on your server. DMARC helps protect your domain from unauthorized use, such as phishing emails, by aligning SPF and DKIM authentication.
Familiarize Yourself with DMARC Policy Options
None (`p=none`): Monitors email traffic without affecting delivery. Useful for testing.
Quarantine (`p=quarantine`): Sends suspicious emails to spam or junk.
Reject (`p=reject`): Blocks suspicious emails from reaching the recipient.
Choose the level that best fits your needs; testing with `none` is often recommended before setting stricter policies.
Log In to Your DNS Hosting Provider
Access your DNS management console on your hosting provider’s site (e.g., GoDaddy, Cloudflare, Namecheap).
Navigate to the section where you can add or edit DNS records.
Create a New TXT Record for DMARC
In the “Host” or “Name” field, enter `_dmarc.yourdomain.com` (replace “yourdomain.com” with your actual domain name).
In the “Value” or “Text” field, enter your DMARC policy.
The basic structure includes the version (`v=DMARC1`), policy (`p=policy`), and email address for reports (`rua=mailto:your-email@domain.com`).
Customize Additional DMARC Options (Optional)
Aggregate Reports (`rua`)
Enter an email to receive regular summary reports on DMARC alignment.
Forensic Reports (`ruf`)
For detailed reports on failed messages.
Failure Option (`fo`)
Customize reporting for specific DMARC failures (e.g., `fo=1` for failures to be reported).
Save and Test Your DMARC Record
Save the DMARC record. Allow some time for DNS propagation, which can range from a few minutes to 24 hours.
Use DMARC testing tools like DMARC Analyzer or MXToolbox to verify that your DMARC record is correctly configured and monitor its effectiveness.
Crosschecking Email Authentication
Here’s how you can check if your MX, SPF, DKIM, and DMARC records are set up correctly:
Check email headers
Send a test email and examine the headers for:
- Received-SPF: If this header shows “pass,” the email passed SPF authentication.
- Authentication-Results: Look for DKIM and SPF entries. If both show “pass,” DMARC authentication also passed.
Use a DNS tool
Tools like MXToolbox or Google Apps Toolbox provide quick checks for your SPF, DKIM, and DMARC records.
Check provider settings
Many email service providers have a “Domains” or “Settings” section where you can verify these records. Correctly set up records will usually display with green checkmarks or “verified” status.
Use the command line
You can use nslookup (short for "Name Server Lookup"). It’s a command-line tool used for querying Domain Name System (DNS) records. It helps network administrators and users retrieve various DNS details, such as IP addresses associated with a domain, the Mail Exchange (MX) records for email routing, or TXT records for SPF, DKIM, and DMARC authentication.
- Open the command line and type `nslookup -type=txt [yourdomain.com]` to check SPF records. If an SPF record exists, you’ll see something like “v=spf1 include:_spf.google.com ~all.” If not, either the record can’t be retrieved, or it doesn’t exist.
- For DKIM, use `nslookup` with the selector and domain name,
e.g., `nslookup -type=txt selector._domainkey.yourdomain.com`.
Address any authentication failures
If records aren’t passing, adjustments to your DNS settings may be needed. Remember that while these records authenticate emails, proper server configurations are essential for the records to be effective in enforcing your domain policies.
These methods will confirm if your MX, SPF, DKIM, and DMARC records are properly set up and functioning.
Email Warm-Up - The Next Step after Email Authentication
Once you’ve set up MX, SPF, DKIM, and DMARC, it’s time to warm up your email. Jumping straight into sending cold emails can hurt deliverability, even with these records in place.
Use a tool like Manyreach that comes with unlimited email warm-ups to warm up your email senders daily for 30 days. This builds your domain’s a positive reputation and helps your emails hit inboxes, not spam.
Start slow, and let the warm-up process work its magic!
.webp)






